CYBER RESILIENCE: 5 CORE ELEMENTS OF A MATURE CYBER RECOVERY PROGRAM
Cyber resilience is the result of business, security, and IT coming together to develop an integrated strategy and roadmap that aligns cyber security and business continuity. Its goal is to transform business expectations and guarantee the business less than significant impact from a cyber-attack.
To achieve this, organizations need to invest in developing and maturing a recovery program that can be reliably called upon it to bring back their business in the event of an attack.
5 ELEMENTS OF CYBER RECOVERY PROGRAM MATURITY AND ACHIEVING INCREMENTAL OUTCOMES
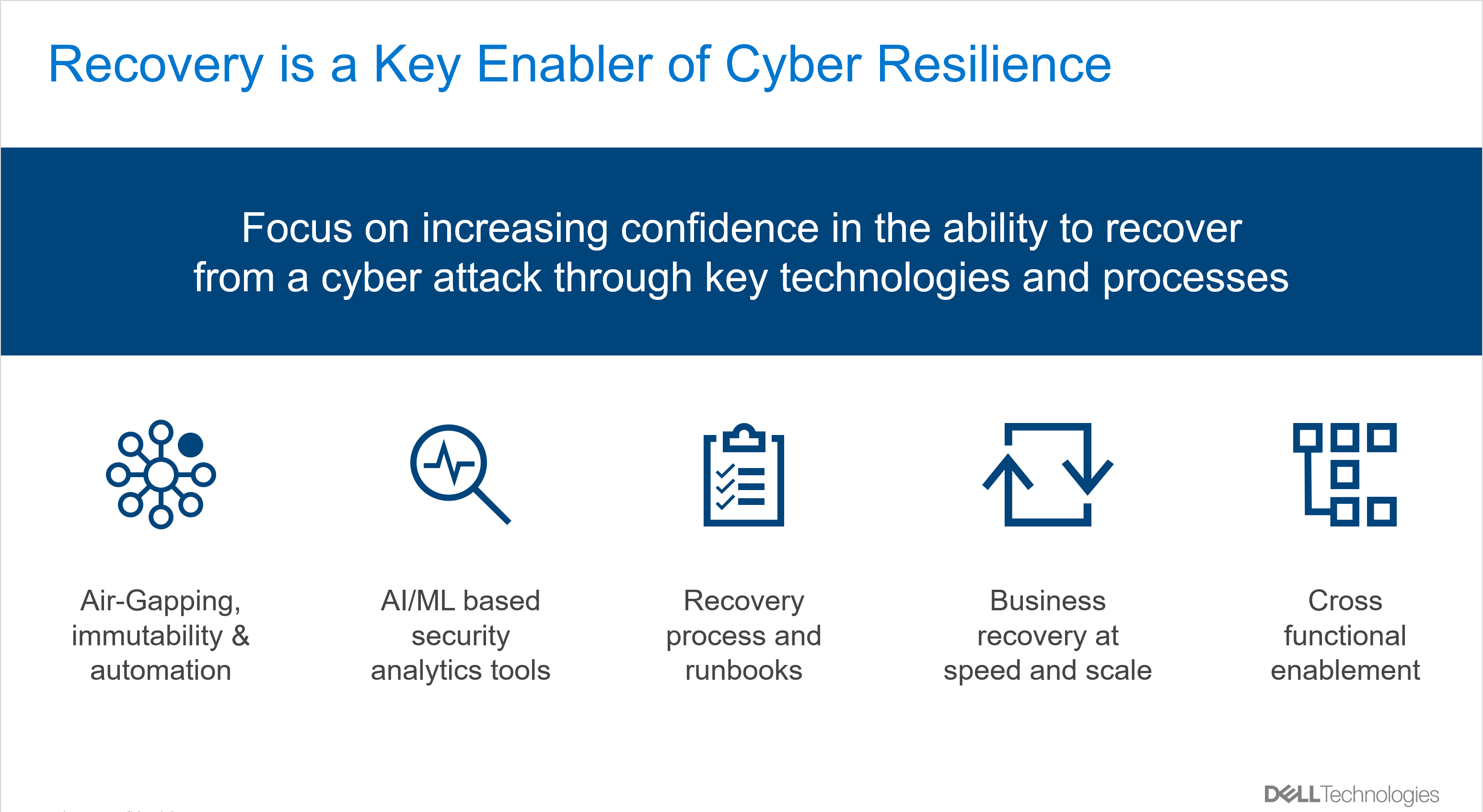
1. Organizations need to utilize technology purpose-built for recovering from a cyber-attack. The latest cyber recovery technologies are designed to address common threat vectors and create an effective cyber vault to protect enterprise data by creating isolation and additional hardening features, such as air-gapping and immutable storage, alongside automation to maintain process integrity and minimal user intervention.
2. Modern malware is a major challenge for organizations due to its sophisticated nature and intent to remain inconspicuous allowing the hackers to go unnoticed until they are ready to strike with force and cause widespread damage. They are known to leverage zero-day vulnerabilities to access and spread the infection, because its signature is not known, and it easily bypasses the traditional security defenses. Continuously analyzing data and analyze behavioral patterns using AI/ML based security analytics tools increases the likelihood of finding indicators of compromise and take proactive action to neutralize the infection before an attack is launched.
3. Developing a recovery processes is critical in operationalizing cyber recovery technologies and being ready for a recovery effort. This process must be tied tightly to recovering the most critical data first and should be documented in a runbook to ensure repeatability. Without careful planning and runbooks, most organizations may not survive a major interruption to the operation of their business, regardless of how mature their technology implementations are. Developing a recovery runbook also acts as a forcing function to identify gaps in current recovery process, people and skills.
4. To deliver business recovery at speed and scale, it’s imperative to mature the cyber recovery program of the organization, tightly aligning recovery procedures with the criticality of specific business processes or application to normal business operations. This enables the core functions of the business to get back up and running as quickly as possible. This is usually a challenging effort because it relies on a deeper understanding of interdependencies of applications and respective data, configuration management and availability of infrastructure resources. While individual application recovery is achievable through runbooks, we find that incorporating an automation strategy is critical for mass recovery. In the case of cyber it is especially important due to the iterative nature of recovery which includes initial recovery, performing forensics and damage assessment and remediation before data can be returned to production.
5. Full cross-functional enablement of the recovery capability further integrates with organization-wide incident response plans and ensures complete adoption and readiness to execute a recovery. Security and business continuity are a shared responsibility and during widespread cyber-attack where applications, network, systems data are compromised, it requires a cross-functional organization to participate in the recovery efforts.
We’re also seeing many customers interested in having some of their cyber resilience initiatives managed for them to reduce risk and improve security operations. A centralized security operation streamlines threat intelligence, detection and response services. In addition to providing 24×7 operations, MSSPs have a wider view of global cyber threats landscape and bring unique insights. Organizations can redirect their resources that have deep institutional knowledge to high value business recovery operations while the provider can help with incident response, coordination and infrastructure recovery.
Integration of these critical technologies and processes enable organizations build their cyber resilience by knowing they have a “last line of defense” and can recover, should they fall victim to an attack.
HOW TO START A CYBER RECOVERY STRATEGY:
There are a few different activities which are great places to start in building your recovery strategy. One is to conduct a current state analysis to establish a baseline and determine areas to invest in. There are a few ways to achieve this, which include a program maturity analysis or a Business Impact Analysis. Both provide different analyses but will help identify specific activities to prioritize.
Another great place to start is with a well-known industry framework to ensure you’re properly evaluating and designing your cyber recovery plans. The NIST Cybersecurity Framework is one that’s been chosen by many organizations because its holistic view and in-depth recommendations.
Author: Arun Krishnamoorthy, Global Strategy Lead for Resiliency and Security, Dell Technologies
Source: https://www.dell.com/en-us/blog/cyber-resilience-5-core-elements-of-a-mature-cyber-recovery-program/
FOR A FREE CONSULTATION, PLEASE CONTACT US